Cinch I.T. President Awarded CRN Next-Gen Solution Provider for 2020
Tuesday, 19 January 2021
2020 Next-Gen Solution Provider Leaders Through their drive and passion, CRN’s inaugural list honors those 40-years-old or younger who have helped propel growth and strategic direction at their companies. Just as the I.T. channel thrives on a steady stream of new, innovative technologies, so too does it require a continual infusion of people with unique
No Comments
How To Reinstall A USB Printer
Thursday, 14 January 2021
With so many more employees working from their home instead of the office, some of us may forget how to reinstall a USB printer. Fortunately, installing a printer in Windows is a painless task with a quick setup. You’ll be able to start printing immediately after you designate a local printer. You can also install
- Published in Tech Blog
5 Cybersecurity Tips To Protect Your Business
Friday, 13 November 2020
Let’s face it: no one likes to think about cybersecurity flaws in their business, much less plan for them. But since businesses all over the country are gearing up for long-term remote work, we want to give you a brush-up on some simple things you can (and should!) be doing to protect your business.
- Published in Tech Blog
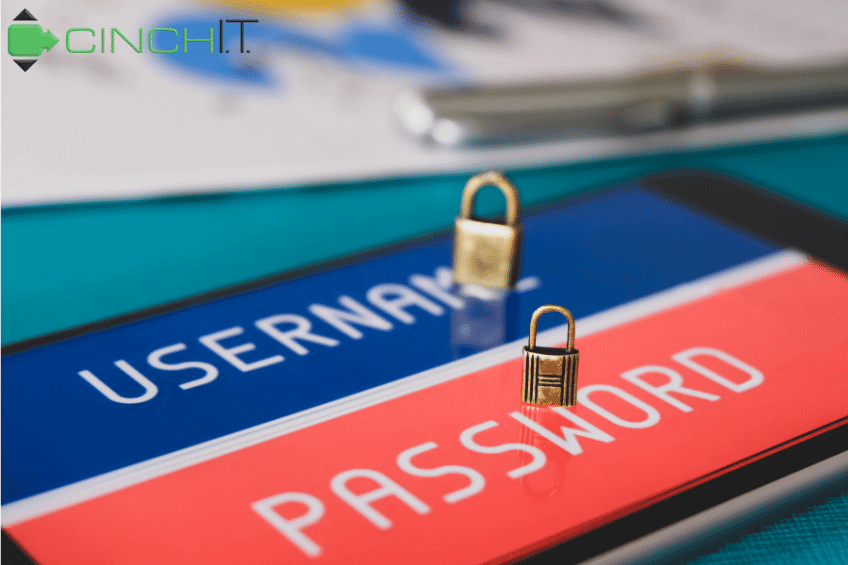
Network Security: How to Protect Your Passwords
Friday, 11 September 2020
You can have all the locks on your data center and all the network security available, but nothing will keep your data safe if your employees are sloppy with passwords. There are many ways data can fall prey to a breach. For example, opening a malicious email link is one of the most common sources
- Published in Tech Blog
Computer Support: 5 Tips to Onboard Remote Employees
Tuesday, 04 August 2020
Remote workforces rely on computer support. Many business owners are asking themselves right now – is a small workforce right for me? Access to better talents, a cut on costs, and improved productivity are all possible advantages. On the other hand, candidates enjoy the flexibility, independence, and work-life balance that comes with distributed labor. When
- Published in Tech Blog
Network Security: Can Your Company Survive a Cyber-Attack?
Tuesday, 21 July 2020
On July 15, several high-profile Twitter accounts were hacked to spread a cryptocurrency scam. Twitter has enterprise-level network security, so how did hackers gain access to these profiles? Twitter reported that the hackers used an internal admin tool to gain access to the accounts. Specifically, the company tweeted that “a coordinated social engineering attack” on
- Published in Tech Blog
Cybersecurity: How to Safely Work from Home
Tuesday, 24 March 2020
As the global COVID-19 pandemic continues to disrupt the U.S. economy severely, cybersecurity has become more crucial than ever. Working from home is no longer a periodic benefit for many Americans but a requirement for many businesses to stay open. However, operating safely and effectively from a remote setup involves extra security measures. While working
- Published in Tech Blog
Windows Possibly Removing Option To Use Outdated Wifi Connections
Wednesday, 07 August 2019
If you haven’t already installed the 1903 Windows 10 update released in May, be advised. When you install it, you’ll start seeing warning popup boxes any time you connect to a WiFi network that is using TKIP (Temporal Key Integrity Protocol) or WEP (Wired Equivalent Privacy) to encrypt and secure those connections. The particulars of
- Published in Tech Blog
Cinch I.T. Franchise Owner Excited to Serve Businesses in Woburn Massachusetts
Monday, 01 July 2019
Cinch I.T.’s newest office is officially open and serving businesses in and around the Woburn, Massachusetts area. Owner and Regional Director, Jay Small, has been serving customers in this area for over a year but has now officially opened his own franchise location. Jay was previously a Senior Account Manager for Cinch I.T. delivering consulting,
- Published in Awards
Cinch I.T. Ranked Among World’s Most Elite 501 Managed Service Providers
Thursday, 20 June 2019
12th Annual MSP 501 Identifies Top Forward-Thinking Global MSPs & Leading Trends in Managed Services JUNE 18, 2019: Cinch I.T. has been named as one of the world’s premier managed service providers on the prestigious 12th-annual Channel Futures MSP 501 rankings. Every year, MSPs worldwide complete an extensive survey and application to report their product
- Published in Awards