
You can have all the locks on your data center and all the network security available, but nothing will keep your data safe if your employees are sloppy with passwords. There are many ways data can fall prey to a breach. For example, opening a malicious email link is one of the most common sources of phishing scams.
Here are some basic practices that you should require your employees to follow. System administrators should implement other policies. These could include forbidding repeat passwords and enforcing lock-outs after failed attempts. But just for you as a manager, here are a few tips.
- Change Passwords Periodically – Most security experts recommend that companies change out all passwords every 30 to 90 days.
- Exceed Password Requirements – Should include a mix of upper and lowercase, number, and a symbol.
- Avoid Identifiable Details – Teach employees to avoid common dictionary words and personal data. This data might include addresses, telephone numbers, SSN, etc.
- Limit Account-Sharing – Emphasize that employees should not access anything using another employee’s login. To save time or for convenience, employees may leave systems open and let others access them. This process ensures that one person doesn’t take the time to log out to force the next employee to log back in. Make a policy regarding this and enforce it.
Essential Password Tips
These are just a few essential password tips that can make a big difference in protecting your business’s cybersecurity.
We all know we need to use strong passwords. Every news story about a data breach or stolen identity is a reminder of this need. But when you look at the most commonly used passwords, it becomes clear that too many business owners neglect their network security. So much so that the 20 most frequently used passwords not only contain highly insecure passwords like the word “password,” they also account for a whopping 10.3% of all passwords that are in use. That’s an astonishingly high number, considering the near-endless combination of possible passwords that can form with just four characters containing upper & lower case letters, numbers, and symbols.
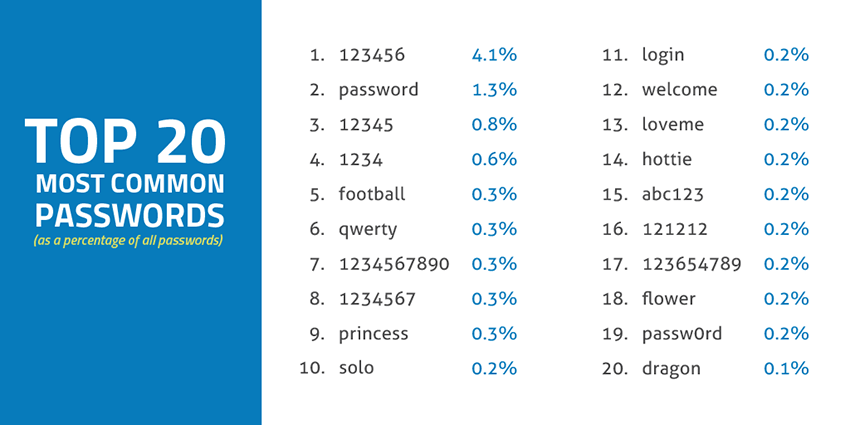 Looking at the top 20 list of passwords makes one thing clear. Even though computing power has continued to demonstrate the ability to crack most passwords in minutes, you don’t need a machine to guess most of the passwords listed above. Using any of the above passwords will probably continue to use them until they face a network security breach. Still, for the rest of us who are serious about proactively protecting our data, there is good news. There is a nearly endless number of hard-to-crack passwords available. The bad news is that most of these are very difficult to remember without some help.
Looking at the top 20 list of passwords makes one thing clear. Even though computing power has continued to demonstrate the ability to crack most passwords in minutes, you don’t need a machine to guess most of the passwords listed above. Using any of the above passwords will probably continue to use them until they face a network security breach. Still, for the rest of us who are serious about proactively protecting our data, there is good news. There is a nearly endless number of hard-to-crack passwords available. The bad news is that most of these are very difficult to remember without some help.
What Makes a Password Strong?
Password strength is directly related to how much computing power is required to crack the password. Security experts recommend that users create long, complex passwords to increase their time to break exponentially. Here are some concrete steps you can take to improve the network security of your accounts:
The longer the password, the better.
Experts recommend creating passwords that contain a minimum of 8 characters. If your password protects something sensitive, like access to your bank account, then use a minimum of 12 characters.
Use everything available on your keyboard.
Numbers, upper and lower case letters, and symbols all help increase your password’s strength drastically.
Throw away dictionary words.
It’s critical never to use common words or names within passwords. This rule can extend one step further to include compounds of multiple words. “IloveLabraDorReTrievers” is not a secure password if the information it’s protecting is of high import.
Avoid commonly used password patterns.
A 2013 DARPA study analyzed a Fortune 100 company that followed five frequent varieties. Three of these password templates included:
- Five lowercase, one uppercase, and three numbers (Example: Komand123)
- Six lowercase, one uppercase, and two numbers (Example: Komando12)
- Three lowercase, one uppercase, and five numbers (Example: Koma12345)
Use unique passwords.
Don’t cycle through the same set of passwords or recycle one across different services. That habit only diminishes the benefit of using a strong password. A cybersecurity study by the University of Cambridge showed that 31% of users reuse passwords in multiple places. When one of those reused passwords becomes compromised, the impact on the user amplifies.
Be careful where you store your passwords.
Your employees should never store their passwords in spreadsheets or upload them to the cloud unless they’re encrypted. Data shows that the average company relies on 143 files that contain the word “password” in the file name. If you’re going to store your password somewhere, use a reputable and secure password manager. P.C. World has a list of the best password managers to optimize your network security.
Two-factor authentication is your friend.
Two-factor protection adds another layer of protection against hackers logging in with a stolen password. With two-factor authentication, you’ll usually need a cell phone to verify your identity.
Keeping Strong Passwords Memorable
The above rules are easy enough to follow. So why aren’t more people following them? There are two primary reasons. First, far too many services don’t require a strong password. Sure, they highlight your password’s strength, but more commonly, they still allow you to save a weak password.
Second, remembering a truly random 12-character password is impossible – unless you have a photographic memory. That’s why far too many people settle for passwords that are weaker and easier to remember than they should. Fortunately, there are a few tricks that can help you create some truly random and secure passwords.
Method #1: Create your password from a sentence
People are much better at remembering sentences and song lyrics than they remember random letters, numbers, and symbols. One trick is to take the first letter of every word in a long memorable sentence. Then, add upper and lower case letters, numbers, and a few symbols to produce your password.
Are you a fan of the Beatles? Then try this: “Yesterday, all my troubles seemed so far away / Now it looks as though they’re here to stay / Oh, I believe in yesterday.” In password form, this converts to “Y,amtssfa/Nilatt’ h2s/O, Ibiy”. Simple enough, right?
Another excellent example is to use a personal statement. “Don’t forget, your wedding anniversary is on October 3rd!” The password then becomes “Df,ywaioO3rd!” There are endless ways to build highly secure and easy to remember passwords using this trick.
Method #2: Treat your keyboard like a constellation
Your keyboard is a blank canvas, ready to help you create your most robust password yet. Draw patterns meaningful to you across the keyboard, including letters and numbers (using your imagination, not permanent marker). The shapes could be your initials, your first name, or a geometrical shape to create your password of choice.
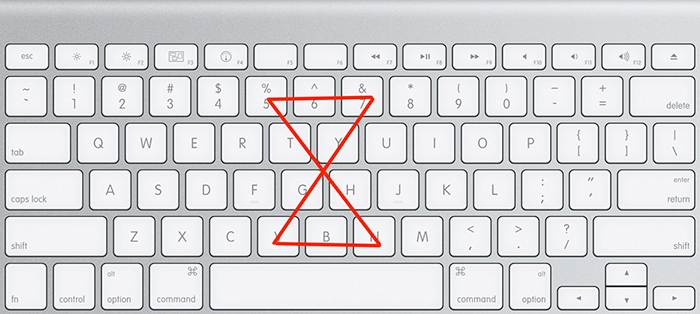
These two methods can generate random, secure passwords that are easy to remember. In addition to strong passwords, experts also recommend turning on multi-factor authentication. Many websites support multi-factor authentication today, including Dropbox, Gmail, and most banking websites. While there’s no fool-proof way to prevent hackers from gaining access to your data, these steps reduce your risk.
Stay Socially Connected
Connect with Cinch I.T. on Facebook, Twitter, LinkedIn, and Instagram with the hashtag #cinchit.
About Cinch I.T.
Since 2004, Cinch I.T. has been providing customer-focused I.T. services for businesses of all sizes. Every element of our computer support offers the fastest and friendliest service in the industry. Cinch is one of the nation’s fastest-growing managed I.T. service franchises with 7 locations and counting. To learn more, visit cinchit.com. For more information about I.T. franchise opportunities, visit cinchfranchise.com.



