AI-Powered Phishing Scams Are Here: Learn How to Stay Protected
Thursday, 25 July 2024
With the advent of generative AI, phishing scams have become more sophisticated than ever. Scammers can now send phishing emails that break language barriers, reply in real-time, and automate mass personalized campaigns almost instantly. The FBI is citing sources that scammers are spoofing domains and accessing sensitive data. As AI gives scammers an edge, how
- Published in Tech Blog
No Comments
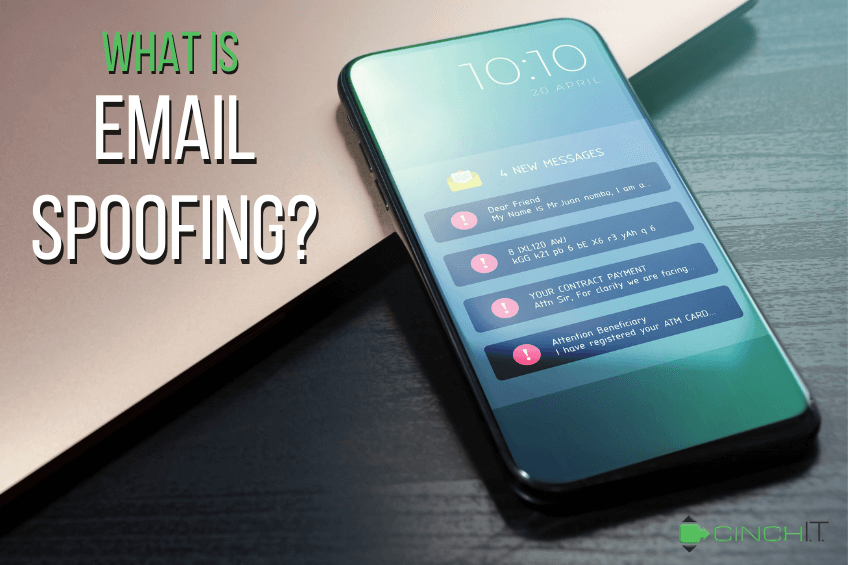
What Is Email Spoofing?
Sunday, 19 May 2024
Email is one of the most common avenues for cyberattacks, and cybercriminals often use it to deliver malicious content. Studies show that approximately 1.2% of all emails sent worldwide are malicious, translating to about 3.4 billion emails daily. But why are email attacks so common? Email is a widely used form of communication, and email-based
- Published in Tech Blog
Watch Out For These 6 Phishing Trends In 2023
Thursday, 13 July 2023
Cybercriminals need to access personal user information or credentials to launch cyberattacks successfully. New phishing trends are the main ways they obtain this information. Why should you care about phishing as an enterprise with secure business I.T. support? Because phishing is becoming more sophisticated, you can be attacked from anywhere, from your office network to
- Published in Tech Blog
Does My Business Actually Need Cybersecurity Insurance?
Tuesday, 20 June 2023
Don’t look now, but we’re about to reveal some secrets. But first, a question: Does your business need cybersecurity insurance? And by “really need,” we don’t mean “it would be nice to have if we win the lottery.” We mean “as essential as that morning coffee that fuels your 9 to 5.” You’re in the
- Published in Tech Blog
I.T. Services: How to Set Exchange 2013 Email Message Size Restriction
Thursday, 17 September 2020
Email support is a primary focus of I.T. services across the country. Email size in Microsoft’s Exchange server plays a vital role in the organization since it acts as an essential factor for bandwidth, storage limit, email queue, CPU utilization, and mailbox size. This knowledgebase article provides a deeper dive into how email size restriction
- Published in Tech Blog
Managed I.T. Services: How to Export Outlook Cached Email Addresses
Wednesday, 16 September 2020
Looking for email managed I.T. services? This knowledgebase article explains how to copy cached Outlook email addresses and add them to a new user profile. This article is intended for I.T. services professionals, if you require assistance with your business email support please contact us! Jump Ahead: Microsoft Office 2003-2007 Microsoft Office 2010-2013 How to
- Published in Tech Blog