
Cyberattacks are on the rise nationwide, and small businesses are among the hardest hit. Across the US, cybercriminals increasingly target SMBs that lack the enterprise-level defenses of larger organizations. According to recent reports, 60% of small businesses shut down within six months of a cyberattack.
This Small Business Cybersecurity Checklist for 2026 outlines 18 essential IT steps every business should take to stay protected, compliant, and resilient in today’s digital landscape.
____________________________________________________________________________
2026 Small Business Cybersecurity Checklist
1. Use Strong Passwords and a Password Manager
Require your employees to use unique, complex passwords, and never reuse them across systems. A business-class password manager helps employees store and generate secure passwords easily. According to the 2023 Verizon Data Breach Investigations Report, stolen credentials remain the most common entry point for attackers.
2. Enable Multi-Factor Authentication (MFA)
Adding a second layer of login protection, like a smartphone app or text code, stops most unauthorized access attempts. Per CISA, MFA blocks 99% of automated attacks.
3. Keep Systems and Software Updated
Automatic updates should be enabled across Windows, macOS, browsers, and third-party applications. Many major ransomware attacks exploit systems that are months or years out of date, despite available patches.
4. Install Antivirus and Endpoint Protection
Modern endpoint protection tools (EDR) use machine learning and behavior analysis to detect viruses, ransomware, and zero-day threats in real time. Cinch IT regularly implements this essential service for our clients.
5. Back Up Data Using the 3-2-1 Rule
Follow this simple rule: keep 3 copies of your data, on 2 different types of media, with 1 copy offsite or in the cloud. Test your backups monthly to ensure you can recover quickly from data loss, hardware failure, or ransomware.
6. Use a Business-Class Firewall and Secure Wi-Fi
Avoid consumer-grade routers. Deploy firewalls that offer threat detection and web filtering. Lock down Wi-Fi with WPA2 or WPA3, and create guest networks to isolate visitor traffic from internal business systems.
7. Segment Your Network
Use VLANs or subnets to isolate sensitive areas of your network, like accounting software or file servers, from guest devices or IoT systems (like smart TVs or security cameras). This limits how far attackers can spread if they get in.
8. Implement Least-Privilege Access
Every user should have access only to the files and systems they need for their role. Regularly review access permissions and promptly revoke accounts for departed employees. This reduces the damage caused by internal misuse or stolen credentials.
9. Secure Admin Accounts Separately
Admin accounts should never be used for day-to-day tasks. Limit who has administrative access, protect those accounts with MFA, and monitor for suspicious activity. This is one of the most important steps to harden your IT environment.
10. Encrypt Devices and Sensitive Data
Turn on full-disk encryption (e.g. BitLocker for Windows or FileVault for Mac). Encrypt databases or files that contain sensitive information like client records or payment info. If a device is lost or stolen, encrypted data stays unreadable.
11. Secure Cloud Platforms
Companies are increasingly moving to Microsoft 365 or Google Workspace. Make sure your organization is using security defaults, enforcing MFA, and limiting public file sharing. Misconfigured cloud settings are one of the top SMB vulnerabilities today.
12. Train Employees on Cybersecurity Best Practices
Human error causes the majority of successful attacks. Train your team to recognize phishing emails, malicious links, and unsafe behavior. According to Coalition, ongoing employee training reduces cyber incidents dramatically.
13. Create an Incident Response Plan
Even small businesses need a simple action plan for cyber incidents. Outline who to contact (IT partner, insurance, law enforcement), how to isolate affected systems, and how to recover operations. Practice it at least once a year.
14. Monitor for Dark Web Leaks
Use a service to monitor whether your company’s emails or passwords have been leaked. Cinch IT offers a free Dark Web Scan, allowing you to catch exposed credentials early and act before criminals use them.
15. Use Business-Grade Email and Filtering
Don’t rely on Gmail or Yahoo for company communications. Platforms like Microsoft 365 or Google Workspace include spam filtering, spoofing protection, and secure delivery. Review your configuration to block common phishing attempts and impersonation.
16. Plan for Business Continuity
Think beyond backups. How would your team function if your office flooded or your internet failed? Cloud-based tools, mobile hotspots, remote work plans, and communication templates all help ensure you can serve your customers even during disruptions.
17. Maintain and Replace Aging Hardware
Using outdated tech increases your risk. Cinch IT recommends replacing business PCs every 4–5 years and avoiding unsupported operating systems. Modern machines are easier to secure, manage, use, and are often more energy-efficient.
18. Partner With a Locally-Based IT Provider
Most SMBs don’t have an internal IT department, and that’s okay! Partnering with a managed IT provider can help your business handle your patching, cybersecurity, backups, helpdesk, and more; all for a set predictable monthly cost.
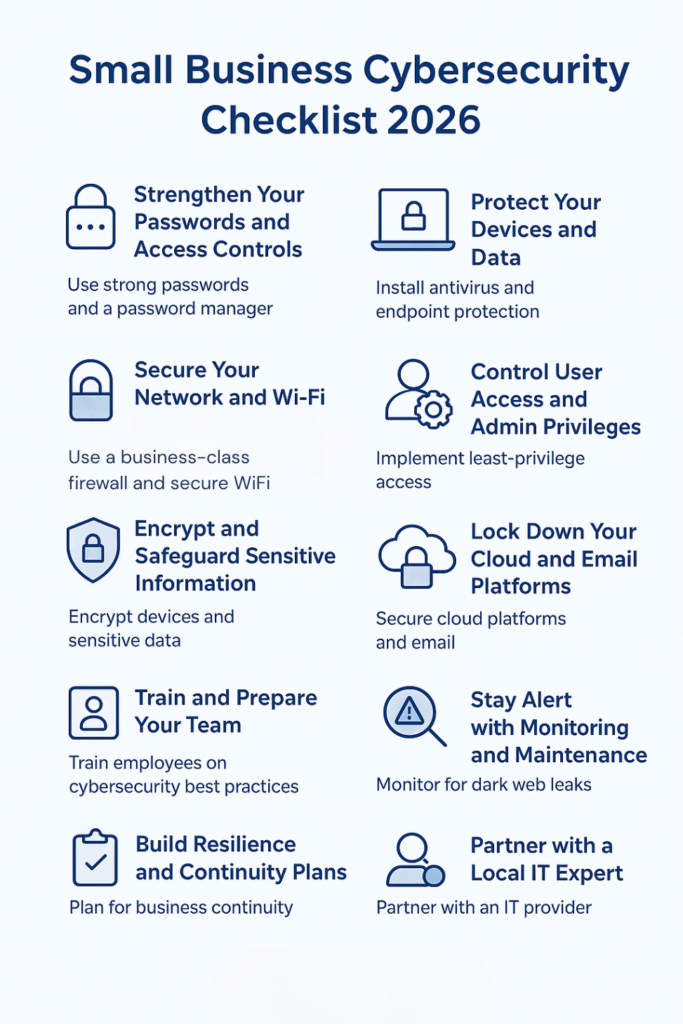
Small business cybersecurity checklist for 2026
____________________________________________________________________________
Conclusion
By following this Small business cybersecurity checklist, your company will be in a stronger position to prevent downtime, avoid data breaches, and stay compliant with growing IT regulations.
Remember to focus on the basics first: MFA, backups, and training, then build toward full resilience. SMBs don’t need to operate at enterprise scale and run enterprise-grade IT, they just need the right checklist. If your business needs help deploying any of these ” Small Business Cybersecurity Checklist” points, Cinch IT is here to help. Our team specializes in cybersecurity, backups, and IT management for SMBs.
____________________________________________________________________________
About the Author
Niko Zivanovich is a Cybersecurity Leader with experience in helping organizations understand and achieve a more complete security posture. He is a co-owner of Cinch IT of Denver and has been working at Pellera Technology Solutions for 6 years, most recently as the Director of Cyber Defense and Threat Intelligence. Niko specializes in CISO advising, netsec ops, incident response, pen testing, and threat intelligence research. He holds multiple certifications through the SANS GIAC organization and is a Board Director for the InfraGard Colorado and Wyoming Chapter.
Enjoy the Small Business Cybersecurity Checklist: 18 IT Must Do Basics for 2026 article? If so then head over to our Blogs for more top tech tips.
____________________________________________________________________________
About Cinch I.T.
Founded on the belief that I.T. support should be easy, Cinch I.T. has grown into one of the nation’s fastest-growing managed service providers. Our franchise model blends centralized expertise with local ownership, giving clients the best of both worlds. Our team is committed to being more than just a service provider, we’re your dedicated partner in achieving operational efficiency and peace of mind. With our fast, friendly, and transparent approach, you’ll always know where you stand.
Discover how Cinch IT can support your success through smarter, more secure technology solutions. Contact us today!
View our nationwide Cinch I.T. offices:


![Tech Tips – 5 Ways to Adapt to Remote Work Support [BLOG] Tech Tips - 5 Ways to Adapt to Remote Work Support - remote work support, I.T. support in Louisville, KY, I.T. support Louisville, Louisville I.T. support, Louisville computer support, computer support Louisville, KY](https://cinchit.com/wp-content/uploads/2022/06/Tech-Tips-5-Ways-to-Adapt-to-Remote-Work-Support-BLOG-370x240_c.png)
