FIND A LOCAL OFFICE NEAR YOU
NATION WIDE
HELPDESK SUPPORT WITH
ONSITE SUPORT IN

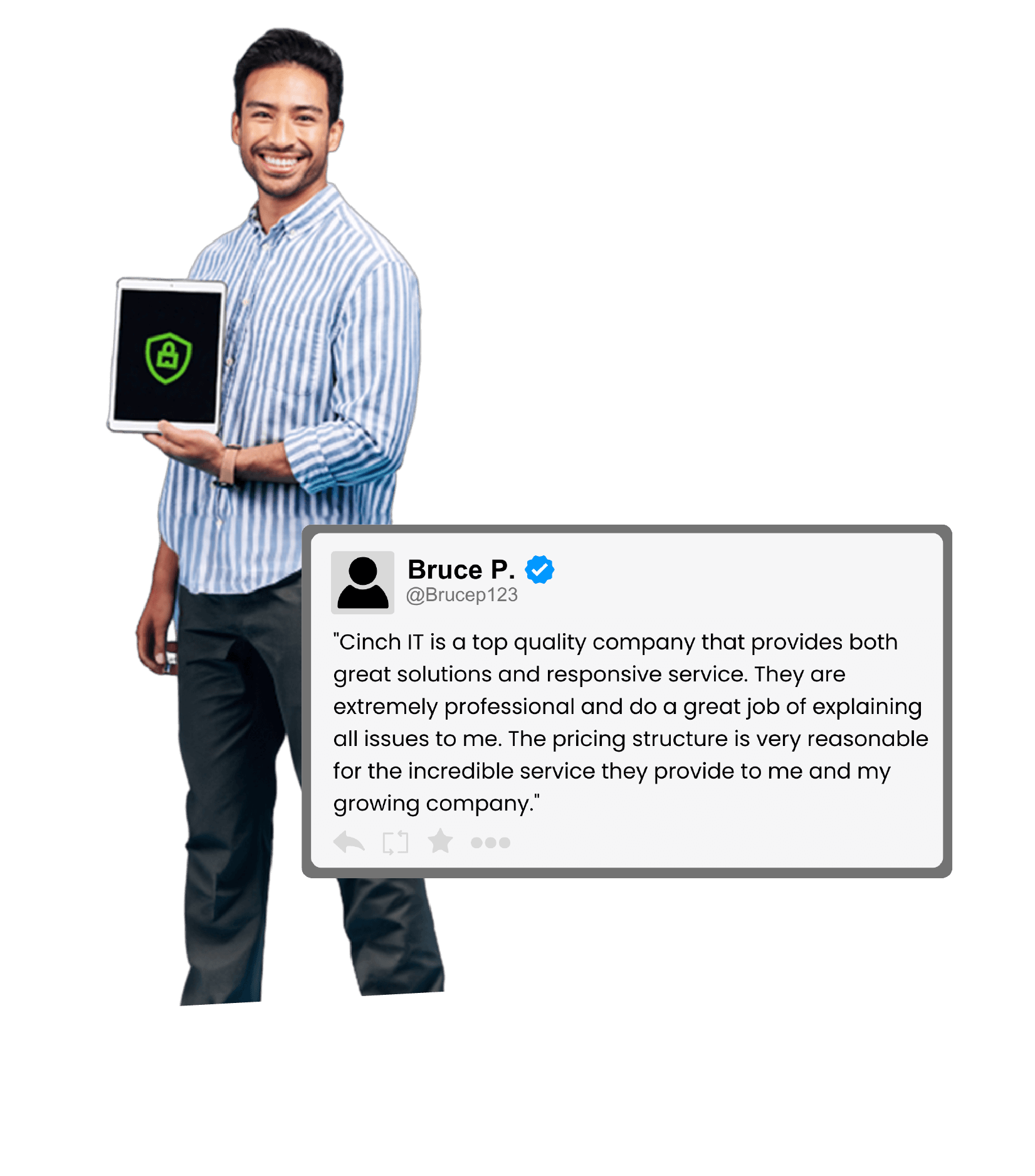
Since 2004, Cinch I.T. has been providing customer-focused managed I.T. services for businesses of all sizes. Every element of our support is designed to provide not only the best I.T. services but also the fastest and friendliest computer support network security in the industry!
Let's Connect
If you are a business owner who is plagued with slow computers, viruses, or email issues, then give Cinch IT a call.
Our consultative, proactive approach will help save you money and enhance productivity.